
Biometric authentication is changing how we prove who we are, using fingerprints, faces or even the way we walk to keep our information safe. Now, get this. More than 70 percent of smartphones sold in South Africa already use biometric sensors every day. That might sound secure, but the real story is not just about fancy tech or convenience. The biggest surprise is how these tools are quietly rewriting the rules for privacy and trust in ways most people have never imagined.
Table of Contents
- Understanding What Is Biometric Authentication
- Types And Examples Of Biometric Authentication
- Benefits And Challenges For South Africans
- Future Trends In Biometric Security
Quick Summary
| Takeaway | Explanation |
|---|---|
| Biometric authentication improves security and convenience | Utilizes unique human traits, offering enhanced security over traditional passwords. |
| Physiological and behavioral biometrics are key | Diverse technologies, like fingerprints and typing patterns, provide different verification methods. |
| South Africa faces unique implementation challenges | Infrastructure and privacy concerns must be addressed for adoption in a diverse society. |
| Future trends include multimodal systems | Combining various biometric methods enhances accuracy and security, reducing fraud. |
| Ethical considerations are crucial for trust | Innovations in privacy protections must accompany tech advancements to secure user confidence. |
Understanding What is Biometric Authentication
Biometric authentication represents a sophisticated security technology that transforms how we verify identity by leveraging unique human physical or behavioral characteristics. Unlike traditional password systems, biometric authentication uses measurable personal traits that are nearly impossible to duplicate or steal.
The Science Behind Biometric Identification
At its core, biometric authentication relies on capturing and analyzing distinctive human features. Academic research from Queensland University of Technology explains that these systems work by collecting specific biological or behavioral data points that create a unique digital signature for each individual. These characteristics can range from physical traits like fingerprints and facial structures to behavioral patterns such as typing rhythm or voice modulation.
The authentication process typically involves three critical stages:
- Data Collection: Scanning and recording specific biometric markers
- Data Processing: Converting physical characteristics into digital templates
- Verification: Comparing captured data against stored reference information
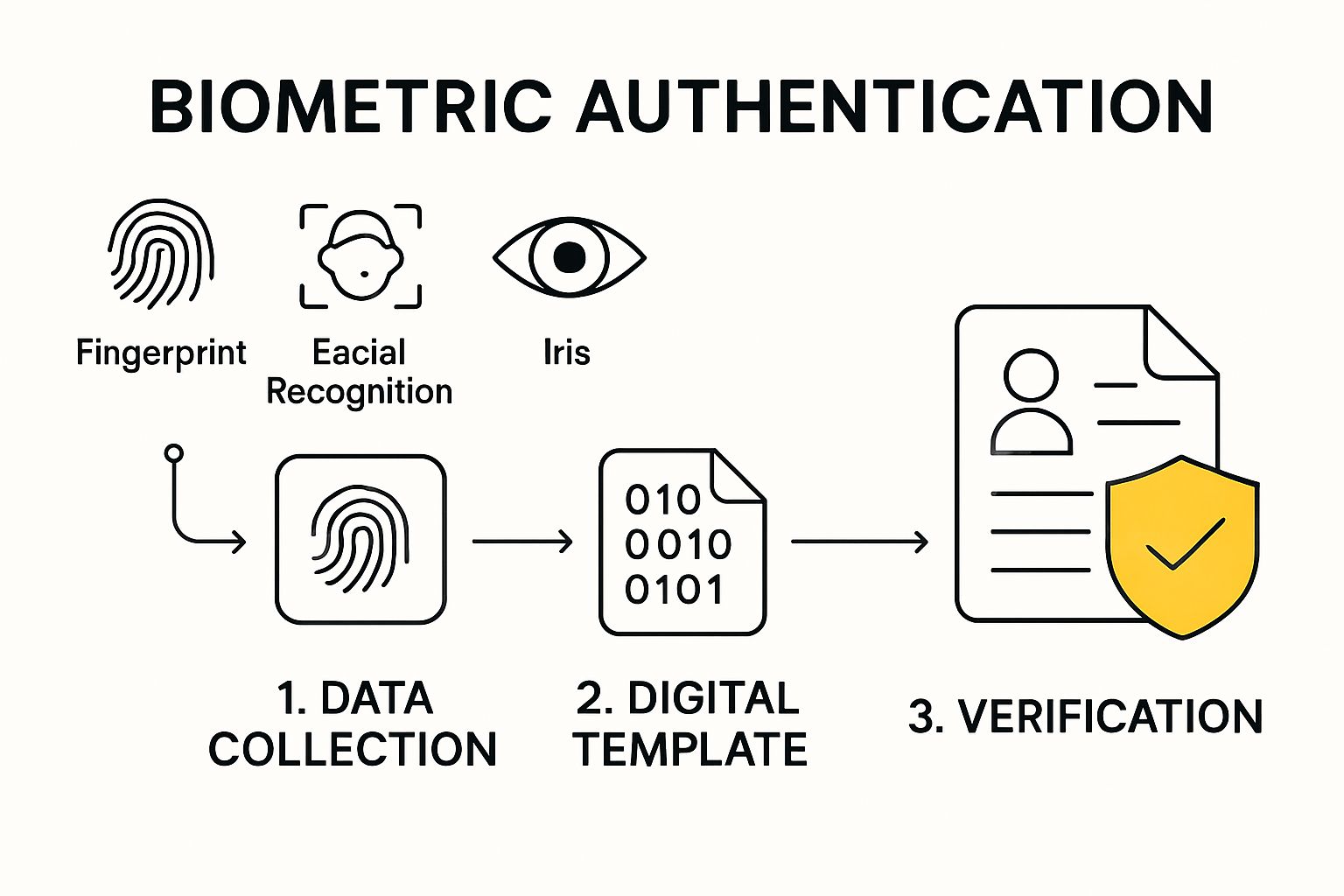
Types of Biometric Authentication Technologies
Modern biometric systems have evolved to incorporate multiple identification methods. Cybersecurity experts from NIST categorize these technologies into several primary categories:
-
Physiological Biometrics: Focused on physical characteristics
- Fingerprint recognition
- Facial recognition
- Iris and retinal scanning
- Hand geometry
-
Behavioral Biometrics: Based on unique interaction patterns
- Signature dynamics
- Keystroke rhythm
- Voice recognition
- Gait analysis
Each biometric method offers distinct advantages and challenges. Fingerprint scanning remains the most widespread, integrated into smartphones and security systems worldwide. Facial recognition has gained significant traction with advanced machine learning algorithms that can detect subtle facial variations with remarkable precision.
The technology continues to advance rapidly, addressing previous limitations in accuracy, processing speed, and user privacy. Modern biometric systems now incorporate sophisticated algorithms that can detect potential spoofing attempts, ensuring a more robust and secure authentication experience.
As digital security becomes increasingly critical, biometric authentication represents a powerful solution that balances convenience with stringent security requirements. By leveraging inherent human characteristics, these technologies offer a more intuitive and challenging-to-compromise approach to identity verification.
Whether protecting personal devices, securing corporate networks, or enabling seamless access control, biometric authentication is reshaping how we think about digital security and personal identification.
Types and Examples of Biometric Authentication
Biometric authentication encompasses a diverse range of technologies that leverage unique human characteristics for secure identification. Encyclopedia Britannica categorizes these systems into two primary domains: physiological and behavioral biometrics, each offering distinct mechanisms for verifying individual identity.
Physiological Biometric Authentication Methods
Physiological biometrics focus on measuring specific physical characteristics that are inherently unique to each individual. TechTarget research highlights several prominent techniques:
-
Fingerprint Recognition: Perhaps the most widespread biometric method, fingerprint scanning analyzes the intricate patterns of ridges and valleys on human fingertips. Modern smartphones and secure access systems frequently utilize this technology.
-
Facial Recognition: Advanced algorithms map facial contours, measuring distances between key facial landmarks to create a unique digital profile. This technology has rapidly evolved, enabling sophisticated identification across security, mobile devices, and surveillance applications.
-
Iris and Retina Scanning: These highly precise methods examine the unique patterns within the human eye. The iris contains complex structures that are as distinctive as a fingerprint, making it an exceptionally secure biometric identifier.
-
Hand Geometry: This technique measures the physical dimensions of a person’s hand, including finger length, width, and overall hand shape. While less precise than other methods, it remains useful in specific access control scenarios.
Behavioral Biometric Authentication Techniques
Behavioral biometrics capture the unique ways individuals interact with technology and perform specific actions. National Center for Biotechnology Information provides insights into these fascinating identification methods:
-
Voice Recognition: Analyzing vocal characteristics such as pitch, tone, and speech patterns creates a unique vocal signature. This technology is increasingly used in voice-activated systems and security authentication.
-
Typing Rhythm: Each person has a distinctive pattern of keystrokes, including typing speed, pressure, and unique pauses between characters. This subtle yet powerful method can provide continuous authentication.
-
Gait Analysis: The way an individual walks creates a unique biomechanical signature. Advanced systems can identify individuals based on their walking pattern, stride length, and body movement.
Emerging and Hybrid Biometric Technologies
The future of biometric authentication lies in combining multiple identification methods to create more robust and secure systems. Researchers are developing hybrid approaches that integrate physiological and behavioral biometrics, enhancing accuracy and reducing potential vulnerabilities.
Some cutting-edge developments include multimodal biometric systems that simultaneously analyze several characteristics, creating a more comprehensive and reliable identification process. These advanced technologies promise to revolutionize security across personal, corporate, and governmental domains.
As biometric technologies continue to evolve, they offer increasingly sophisticated solutions for identity verification, balancing enhanced security with user convenience. The ongoing refinement of these systems suggests a future where digital security becomes more intuitive, personalized, and challenging to compromise.
Below is a table comparing common biometric authentication methods, summarising their core characteristics and typical use cases for quick reference.
| Authentication Method | Type | Unique Trait Used | Typical Use Cases |
|---|---|---|---|
| Fingerprint Recognition | Physiological | Fingerprint patterns | Smartphones, banking, access control |
| Facial Recognition | Physiological | Facial structure | Smartphones, surveillance, airports |
| Iris/Retina Scanning | Physiological | Eye patterns | High-security access, border control |
| Hand Geometry | Physiological | Hand shape and size | Workplace access, time tracking |
| Voice Recognition | Behavioral | Vocal characteristics | Call center security, voice assistants |
| Typing Rhythm | Behavioral | Keystroke dynamics | Continuous authentication, IT security |
| Gait Analysis | Behavioral | Walking pattern | Surveillance, healthcare monitoring |
Benefits and Challenges for South Africans
Biometric authentication presents a transformative technological opportunity for South African consumers and businesses, offering sophisticated solutions to longstanding security and identification challenges. National Academies of Sciences research highlights the nuanced landscape of biometric technologies, particularly relevant in a diverse and rapidly digitalizing market like South Africa.
Advantages for South African Users
The implementation of biometric authentication brings significant benefits tailored to the unique South African context. Digital security becomes more accessible and intuitive, addressing critical challenges in personal and professional identification. Key advantages include:
- Enhanced Financial Security: Biometric technologies provide robust protection against banking fraud, a persistent concern in South Africa’s developing financial ecosystem
- Simplified Government Services: Streamlined authentication for identity verification, reducing bureaucratic complexities
- Reduced Identity Theft: Advanced verification methods make fraudulent access significantly more challenging
Technical and Social Challenges

Medical research from Cureus emphasizes the complex considerations surrounding biometric implementation. South Africa faces unique obstacles in widespread adoption:
- Infrastructure Limitations: Varying levels of technological access across urban and rural regions
- Privacy Concerns: Significant apprehensions about personal data collection and potential misuse
- Technological Equity: Ensuring fair and inclusive access across diverse socioeconomic groups
Below is a summary table outlining the main benefits and challenges identified for biometric authentication in the South African context.
| Aspect | Key Points/Examples |
|---|---|
| Benefits | Better financial security, simplified government services, reduced identity theft |
| Technical Challenges | Gaps in infrastructure between urban and rural areas, limited access for some communities |
| Social Challenges | Concerns about privacy and data misuse, need for technological equity and fair access |
| Economic/Cultural | Requirement for public trust, inclusive communication, and protective legal frameworks |
Economic and Cultural Adaptation
The successful integration of biometric authentication requires more than technological implementation. It demands a comprehensive approach addressing cultural perceptions, technological literacy, and systemic trust. South African organizations must focus on:
- Transparent communication about data protection
- Building public understanding of biometric benefits
- Creating accessible implementation strategies
- Developing robust legal frameworks protecting individual privacy
These considerations are crucial in a nation experiencing rapid digital transformation. Biometric technologies offer immense potential to revolutionize security, financial services, and governmental interactions, but their success depends on thoughtful, inclusive implementation.
As South Africa continues to position itself as a technological innovator, biometric authentication represents a critical opportunity to enhance security, improve service delivery, and create more efficient digital ecosystems. The journey involves balancing technological advancement with cultural sensitivity and individual rights.
Future Trends in Biometric Security
The landscape of biometric security is rapidly evolving, driven by technological advancements, increasing digital complexity, and emerging global security challenges. National Academies of Sciences research indicates that future biometric technologies will transcend current limitations, offering more sophisticated, adaptive, and intelligent authentication mechanisms.
Continuous Authentication and Advanced Machine Learning
Traditional biometric systems relied on single-point verification, but emerging technologies are shifting towards continuous authentication. This revolutionary approach monitors user identity throughout an entire digital session, creating a dynamic security environment. Machine learning algorithms will enable systems to:
- Detect subtle behavioral changes in real time
- Adaptively adjust security protocols
- Recognize micro-patterns indicating potential unauthorized access
- Create more nuanced user profiles that go beyond static biometric markers
Multimodal and Hybrid Biometric Systems
Future biometric security will increasingly integrate multiple identification methods, creating more robust and resilient authentication frameworks. These hybrid systems will combine:
- Physiological characteristics like fingerprints and facial recognition
- Behavioral patterns such as typing rhythm and voice modulation
- Advanced contextual data including geolocation and device interactions
By synthesizing diverse authentication signals, these systems will dramatically reduce fraudulent access risks and enhance overall security infrastructure.
Ethical Considerations and Privacy Innovations
As biometric technologies become more sophisticated, ethical frameworks and privacy protections will evolve simultaneously. Key developments will include:
- Advanced encryption techniques for biometric data storage
- Decentralized authentication protocols
- User-controlled consent mechanisms
- Transparent data usage policies
These innovations aim to balance technological advancement with individual privacy rights, addressing growing concerns about potential misuse of personal biological information.
The future of biometric security represents a fascinating convergence of artificial intelligence, human-centric design, and advanced cybersecurity strategies. As technologies become more intelligent and adaptive, authentication will transform from a binary access control mechanism into a comprehensive, contextual security ecosystem.
Emergent trends suggest we are moving towards a future where digital identity verification becomes seamless, intelligent, and fundamentally more secure. The integration of advanced machine learning, multimodal authentication, and robust ethical frameworks will redefine how we understand and implement digital security in the coming years.
Frequently Asked Questions
What is biometric authentication?
Biometric authentication is a security process that uses unique physical or behavioral characteristics of individuals, such as fingerprints, facial recognition, or voice patterns, to verify identity. Unlike traditional passwords, biometric authentication is difficult to replicate or steal, enhancing security.
What are the types of biometric authentication methods?
Biometric authentication methods can be categorized into physiological and behavioral biometrics. Physiological methods include fingerprint recognition, facial recognition, iris scanning, and hand geometry. Behavioral methods involve voice recognition, typing rhythm, and gait analysis, each utilizing distinct human traits for identification.
What are the benefits of biometric authentication for South Africans?
Biometric authentication offers significant benefits for South Africans, including enhanced security in financial transactions, simplified government services, and reduced identity theft. These technologies provide a more reliable means of verifying identity in a diverse and evolving digital landscape.
What challenges does South Africa face in adopting biometric authentication?
South Africa faces several challenges in adopting biometric authentication, including infrastructure limitations between urban and rural areas, privacy concerns regarding personal data usage, and ensuring equitable access to technology across various socioeconomic groups.
Level Up Your Digital Security with Tech That Truly Protects
Stressed about the real risk of identity theft or fraud as highlighted in our article on biometric authentication? Like many South Africans, keeping your private data safe is more urgent than ever. Whether you worry about the safety of your mobile banking or want more control over your personal tech, choosing the right devices is the first step to peace of mind. At PMC Jewellery, we understand the value of secure smart wearables, smart home devices, and accessories that are compatible with the latest biometric authentication technologies. Our best-selling tech collection is packed with products featuring the newest in fingerprint recognition, secure access, and identity protection features, making advanced security straightforward and accessible.
Feel the confidence of shopping with South Africa’s leading multi-category marketplace. With strict quality checks, trusted local fulfillment, and tech options that fit every lifestyle, you can boost your security without breaking the bank. Do not wait until your security is compromised – browse our smart tech range and upgrade to products that keep your digital life locked tight. Ready to secure your future? Visit PMC Jewellery and take charge of your digital protection today.
Recommended
- For Samsung Galaxy Watch 3 45mm Discoloration in Light TPU Watch Band( – PMC Jewellery
- For Samsung Galaxy Watch 3 41mm 20mm Carbon Fiber Striped Silicone Wat – PMC Jewellery
- What Does a MagSafe Case Do? Essential 2025 Guide for Smart Buyers – PMC Jewellery
- For Samsung Galaxy Watch 3 45mm Discoloration in Light TPU Watch Band( – PMC Jewellery
